- Cisco Anyconnect Lose Internet Connection
- Why Does Cisco Anyconnect Keep Reconnecting
- How To Prevent Cisco Anyconnect From Disconnecting
We have a handful of users who lose their split-dns functionality after they are connected to the VPN for awhile. Basically regular internet resolution works and the tunnel actually still stays active. (They can ping internal resources by IP only). As per the suggestion, went to Control Panel- Network and Internet - Network and sharing center But could not find the Cisco AnyConnect secure mobility client connection. Here’s the message ffrom the the cisco anyconnect client ver 4.3.03xxx on Windows10 11:47:31 PM Contacting xxx country 11:47:32 PM Posture Assessment: Required for access.
- When I use the VPN to connect to my office, my internet connection gets disconnected. This was done at my work place for security reasons. In my pc, I have 2 networks cards. One ethernet and one wifi. I have connected to the internet using both these cards. I thought with this setting, the vpn will use one internet and leave the other untouched.
- A user running Internet Connection Sharing is having trouble installing the Cisco 3000 VPN client This is an easy one to fix. The user needs to disable ICS on his machine before installing the VPN.
- In my experience with TM 1300 in D600 XP Pro, wireless connection via TM 1300 works perfectly fine via any WiFi AP or Router, but when I open Cisco VPN client(VPN 5000 Client 5.2.3 3DES, old and EOF vpn box but no $ to upgrade) via WiFi I lose both internet/VPN connection in about 10 minutes or so.
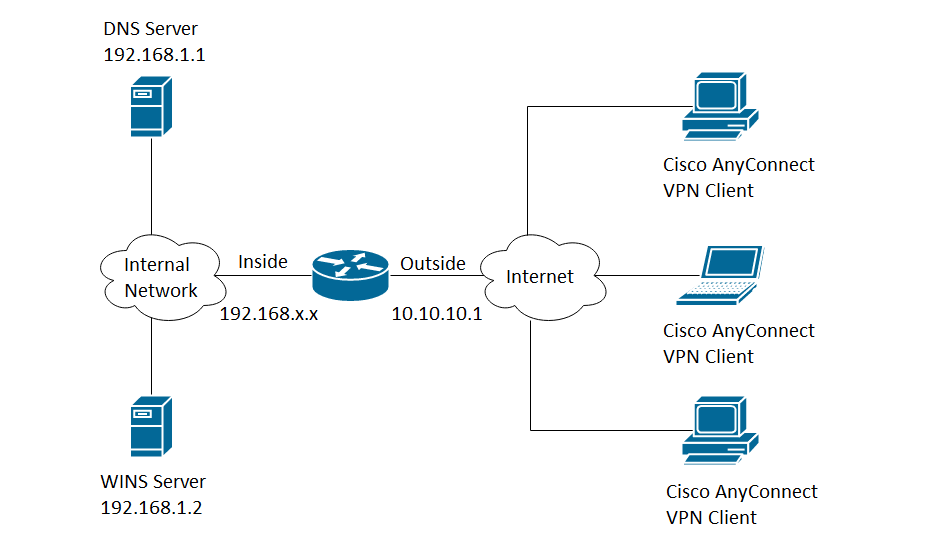
The logs in the ASA indicated that the user session was being terminated on the remote end:
%ASA-5-722037: Group
ASA/pri/act#show vpn-sessiondb anyconnect
Session Type: AnyConnect
Cisco Anyconnect Lose Internet Connection
Username : USERA Index : 229
Assigned IP : x.x.x.x Public IP : x.x.x.x
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Essentials
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)DES DTLS-Tunnel: (1)DES
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1 DTLS-Tunnel: (1)SHA1
Bytes Tx : 699061 Bytes Rx : 245379
Group Policy : GroupPolicy_VPN Tunnel Group : VPN
Login Time : 10:37:45 EST Tue Feb 26 2013
Duration : 0h:41m:04s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
Username : USERB Index : 236
Assigned IP : x.x.x.x Public IP : x.x.x.x
Protocol : AnyConnect-Parent SSL-Tunnel
License : AnyConnect Essentials
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)DES
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA1
Bytes Tx : 59422 Bytes Rx : 36304

Group Policy : GroupPolicy_VPN Tunnel Group : VPN
Login Time : 11:15:31 EST Tue Feb 26 2013
Duration : 0h:01m:18s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
This command actually led me to figuring out the solution. The part where it says 'DTLS-Tunnel' on the working connection, but not the bottom connection, was where the issue was. See, the DSL router I was going through had an outbound filter setup to allow port 443/tcp only, NOT 443/udp.
After reading online about this, I learned that the AnyConnect SSL VPN connection first tries to connect over 443/tcp (TLS), then if successful, transitions over to 443/udp (DTLS). The problem was the connection would establish, but since 443/udp was blocked, it would time out and terminate the connection.
Why Does Cisco Anyconnect Keep Reconnecting
In the ASA, I figured out the following command to run in order to disable the DTLS part of the connection, and force it to only use TLS, since that was what was open to me.
webvpn
How To Prevent Cisco Anyconnect From Disconnecting
Once I turned DTLS off in my group policy, the connection established and stayed up correctly after that.
The following text I found somewhere on Cisco's support forum site, linked here, which helped me figure out the issue.
The SSL-Tunnel is the TCP tunnel that is first created to the ASA. When it is fully established, the client will then try to negotiate a UDP DTLS-Tunnel. While the DTLS-Tunnel is being established, data can pass over the SSL-Tunnel. When the DTLS-Tunnel is fully established, all data now moves to the DTLS-tunnel and the SSL-tunnel is only used for occasional control channel traffic. If something should happen to UDP, the DTLS-Tunnel will be torn down and all data will pass through the SSL-Tunnel again.
The decision of how to send the data is very dynamic. As each network bound data packet is processed there is a point in the code where the decision is made to use either the SSL connection or the DTLS connection. If the DTLS connection is healthy at that moment, the packet is sent via the DTLS connection. Otherwise it is sent via the SSL connection.
The SSL connection is established first and data is passed over this connection while attempting to establish a DTLS connection. Once the DTLS connection has been established, the decision point in the code described above just starts sending the packets via the DTLS connection instead of the SSL connection. Control packets, on the other hand, always go over the SSL connection.
The key point is if the connection is considered healthy. If DTLS, an unreliable protocol, is in use and the DTLS connection has gone bad for whatever reason, the client does not know this until Dead Peer Detection (DPD) occurs. Therefore, data will be lost over the DTLS connection during that short period of time because the connection is still considered healthy. Once DPD occurs, data will immediately be set via the SSL connection and a DTLS reconnect will happen.
The ASA will send data over the last connection it received data on. Therefore, if the client has determined that the DTLS connection is not healthy, and starts sending data over the SSL connection, the ASA will reply on the SSL connection. The ASA will resume use of the DTLS connection when data is received on the DTLS connection.'
The following text I found somewhere on Cisco's support forum site, linked here, which helped me figure out the issue.
The SSL-Tunnel is the TCP tunnel that is first created to the ASA. When it is fully established, the client will then try to negotiate a UDP DTLS-Tunnel. While the DTLS-Tunnel is being established, data can pass over the SSL-Tunnel. When the DTLS-Tunnel is fully established, all data now moves to the DTLS-tunnel and the SSL-tunnel is only used for occasional control channel traffic. If something should happen to UDP, the DTLS-Tunnel will be torn down and all data will pass through the SSL-Tunnel again.
The decision of how to send the data is very dynamic. As each network bound data packet is processed there is a point in the code where the decision is made to use either the SSL connection or the DTLS connection. If the DTLS connection is healthy at that moment, the packet is sent via the DTLS connection. Otherwise it is sent via the SSL connection.
The SSL connection is established first and data is passed over this connection while attempting to establish a DTLS connection. Once the DTLS connection has been established, the decision point in the code described above just starts sending the packets via the DTLS connection instead of the SSL connection. Control packets, on the other hand, always go over the SSL connection.
The key point is if the connection is considered healthy. If DTLS, an unreliable protocol, is in use and the DTLS connection has gone bad for whatever reason, the client does not know this until Dead Peer Detection (DPD) occurs. Therefore, data will be lost over the DTLS connection during that short period of time because the connection is still considered healthy. Once DPD occurs, data will immediately be set via the SSL connection and a DTLS reconnect will happen.
The ASA will send data over the last connection it received data on. Therefore, if the client has determined that the DTLS connection is not healthy, and starts sending data over the SSL connection, the ASA will reply on the SSL connection. The ASA will resume use of the DTLS connection when data is received on the DTLS connection.'
